Surviving the Storm: Navigating the Long-Term Fallout of Data Breaches

At Lewis IT, we believe that data is not just an asset; it's the very heartbeat of businesses, driving operations, strategic decisions, and customer engagement. Yet, lurking beneath the digital transformation's promises lies a formidable adversary: the ever-present threat of data breaches. More than just a temporary hiccup, data breaches can cast long shadows, affecting businesses for years and consuming nearly half of their costs in the aftermath.
The Hidden Aftermath of Data Breaches
The 2019 cybersecurity incident at First American Title Insurance Co., resulting in a $1 million fine by the New York Department of Financial Services (NYDFS) announced in 2023, serves as a stark reminder of the enduring impacts of data breaches. With over 880 million documents compromised, this breach underscores the complex legacy of data vulnerabilities, from financial burdens to reputational damage.
We’ll take a look at the long-term consequences of a data breach. As well as examine a real-world example. You’ll see how a single breach can have enduring implications. Ones that impact a business's reputation, finances, and regulatory standing.
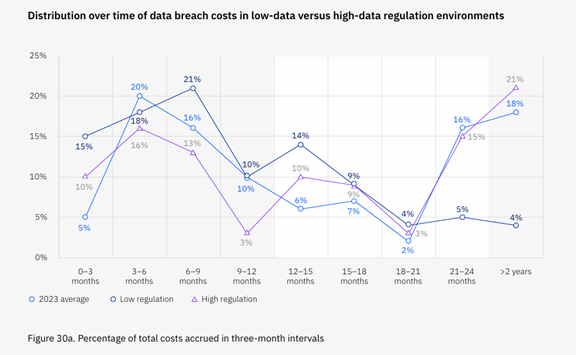
The Enduring Costs of Data Vulnerabilities
Financial Repercussions
The financial burden of a data breach is multifaceted, encompassing immediate costs like detection and containment, as well as long-term expenses such as legal battles, regulatory fines, and compensation claims. These expenditures underline the profound financial strain breaches place on businesses.
Reputational Harm
Perhaps the most lasting impact of a data breach is the erosion of customer trust. The journey to rebuild a company's reputation is arduous, requiring significant investment in public relations and security enhancements to reassure wary stakeholders of the company's commitment to their privacy.
Increased Regulatory Oversight
Post-breach, companies often find themselves under the microscope of regulatory bodies, facing stringent compliance demands, fines, and mandates for security upgrades, further straining resources and finances.
Operational Interruptions
The operational upheaval in the wake of a breach can derail business processes, diverting attention from growth initiatives to damage control, a disruption that can stall progress and adaptation for years.
Challenges in Customer Loyalty and Growth
The ripple effects of a data breach extend to customer retention and acquisition, as trust diminishes and potential clients hesitate to engage, stifling growth and market position.
A Wake-Up Call for Proactive Cybersecurity
The tale of First American Title Insurance Co. is a cautionary narrative for businesses everywhere, illustrating the critical importance of proactive cybersecurity measures. In the face of escalating cyber threats, investing in robust security protocols is not just about prevention; it's about ensuring the longevity and resilience of your business.
The cost of a data breach extends beyond immediate financial losses to touch every facet of a business, from its financial health to its market reputation and operational efficacy. Learning from real-world breaches and prioritizing comprehensive cybersecurity strategies is essential for businesses aiming to protect their futures.
Protect Your Business Before It's Too Late
In an era where cyber threats loom large, conducting a thorough cybersecurity assessment is a crucial step towards safeguarding your network and assets. Whether it's securing endpoints or cloud tools, understanding and mitigating your risks can prevent the far-reaching consequences of a data breach.
Don't wait for a breach to rethink your cybersecurity posture. Schedule a cybersecurity assessment with our experts today and take a decisive step towards securing your business's future. Contact us to learn how we can help you navigate the complex landscape of cyber threats and ensure your organization's enduring success.
Article used with permission from The Technology Press.
Contact Us:
240-201-3732
info@lewisit.io

